Since the dawn of the internet, people have logged into websites, apps, and accounts in one way. Username and password. Since the dawn of the internet, there have been hackers and malicious actors trying to break this system. Hackers have gotten much better since then — new techniques, new technologies, new systems. Why haven’t our login systems caught up?
We 3.0 platforms have moved on — to cryptographic signatures. But Web 2.0 is stuck trying to make the username + password system ‘more secure’. Using stronger, unique passwords, two-factor authentication, and password managers. Unfortunately, each of these is woefully inadequate in the face of attacks. Brute force attacks can and do crack even strong and unique passwords all the time. Most people do not even use strong, unique passwords as remembering so many of them is impossible. Two-factor authentication is also fallible as it adds only one more hackable layer of protection.

Password managers seemed to be the solution. Services that generate strong, unique passwords for all your accounts and store them securely on the cloud. Except, that hasn’t been the case. The recent hacking of LastPass, one of the most popular password managers, has proved this. Hackers in 2022 were able to steal several users’ names, IP addresses, billing addresses, and even their entire password vaults. That means hackers gained access to every single password a user had — to their every single account.
As the internet becomes more central to our lives, this weakness becomes more dangerous and costly. People store their banking information, addresses, sensitive data, and even biometric data online. If the only thing standing between this information and malicious actors is a password or cloud software, privacy doesn’t stand a chance.
Cybercrimes will cost the world an unbelievable USD 10.5 Trillion by 2025. Innovation is desperately needed.
The Web 3.0 Fix
Fortunately, there is a rising industry that values privacy and data autonomy over all other things — Web 3.0. And it is rising to the challenge of hacking. A recent proposal for the updating of Ethereum — a leading blockchain — has a solution. Cryptographic signatures.

Cryptographic Signatures
Blockchain-based platforms and dApps have already the username + password model with cryptographic signatures.
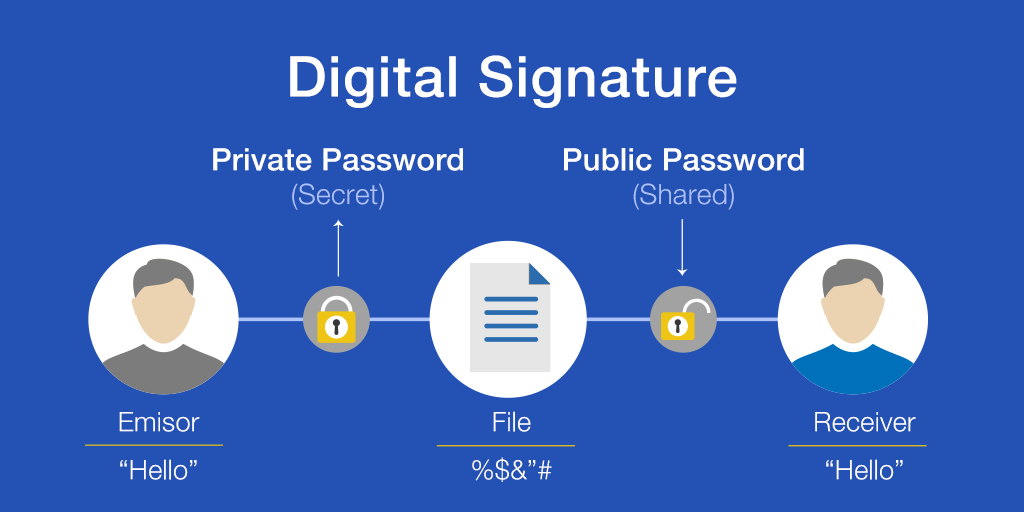
What is a Cryptographic Signature?
A cryptographic signature is a string of characters (like a password) generated using a complex mathematical algorithm. This makes it very strong, unique and impossible to brute-force hack. Every user is assigned one unique cryptographic signature. This one ‘password’ can be used to verify their identity across platforms.
A crypto wallet has two identifiers or ‘keys’ that are checked against each other to verify that the person signing in is really the owner. This is the private key or the cryptographic signature and the public key. The public key is the publicly available identity of the wallet that is shared to make transactions — like a bank account number. The cryptographic signature is like the password or PIN for that bank account.
How do Cryptographic Signatures Work?
- A user sends an encrypted message to a platform along with a unique digital signature
This digital signature is a mathematical combination of the user’s public key and private key.
- The platform uses a verification algorithm to check whether the encrypted message can be decoded with the public key.
- If it can, then the private key is the same as the one connected to the crypto wallet.
What Makes them More Secure?
The digital signature method is more secure because it allows a platform to verify a user’s identity without ever having access to their ‘password’ (the cryptographic signature — their private key). The algorithm used to generate the signature is a ‘one-way function’ something that is impossible to reverse engineer. Finally, a unique digital signature is generated for every log-in request or ‘message’ making it impossible for a hacker to reuse or predict a signature.
The cryptographic signature as a whole also has several advantages over the old way:
Complexity
Cryptographic signatures are much more complicated and longer than normal passwords, making them much harder for a hacker to crack. They are also entirely random as they are generated by an algorithm, and are one of a kind, making them impossible to predict.
Decentralisation
Passwords are generally stored on the cloud — whether on a browser, with the platform or on a password manager. This gives hackers one point of attack and makes passwords very vulnerable.
The cryptographic signature is known only by the user and stored only with them, either as an encrypted file on their device or in ‘cold storage’ (such as an envelope or USB drive). This makes even accessing the signature almost impossible, as it is not stored in a central, public location.
Points of Failure
Most passwords have a mechanism that allows them to be reset, usually by email. This means that if a hacker gains access to a user’s email, they can access all their accounts by resetting passwords. There is a single point of failure, making the entire system very weak.
Cryptographic signatures can only be compromised if a hacker has access to the physical device or cold storage unit that the key is on. There is no way for a hacker to gain access over the internet or the cloud. This means an end to the kind of large-scale privacy leaks that have plagued popular platforms.
Additional Measures
Cryptographic signatures can further be protected by sharding them — dividing the data into parts scattered across devices. This would require a hacker to hack every single node to gain access to the signature.
Larger accounts can also use the multi-signature verification process which would require multiple parties to sign a message before it can be authenticated. This increased decentralisation once again makes hacking almost impossible.
Using hardware wallets or cold storage completely thwarts any cyberattacks by not storing the cryptographic signature on a network at all.
The Future of Data Privacy
In short, a cryptographic signature model means users can have one password for every account. A password that is completely unhackable by either prediction, cloud data breaches, or brute force. They can verify their identity on all platforms without ever actually sharing this password with any of them. This is the future of data security and privacy. This is the end of hacking and data leaks.
Users will no longer have to manage and remember multiple passwords or worry about their account integrity. Platforms will no longer have to worry about malicious actors gaining access to their systems, or leaking sensitive user data. How many scandals can be avoided, and how much money saved?
Cryptographic signatures are already the standard for Web 3.0 platforms and applications, and this Ethereum update allows everyone else to catch up.

